How to Turn On or Off BitLocker for Windows 8 OS Drive with or without TPM
BitLocker Drive Encryption provides protection for operating system drives, fixed data drives, and removable data drives that are lost or stolen. BitLocker does this by encrypting the contents of drives and requiring users to authenticate their credentials to be able to access the information. Encrypting the entire Windows 8 operating system drive on the hard disk encrypts all user files and system files on the OS drive, including the swap (page) files and hibernation files.
This tutorial will show you how to turn on or off BitLocker to encrypt or decrypt the operating system drive in Windows 8 and 8.1 with or without a TPM.
You must be signed in as an administrator to be able to do the steps in this tutorial.
- For computers that boot natively with UEFI firmware, BitLocker requires at least one FAT32 partition for the system drive and one NTFS partition for the operating system drive.
- For computers with legacy BIOS firmware, BitLocker requires at least two NTFS disk partitions, one for the system drive and one for the operating system drive.
- The system drive partition must be at least 350 MB and set as the active partition. If you do not have a system partition, then BitLocker will check for and create one automatically if able step 7 in OPTION ONE below.
- To be able to automatically unlock fixed data drives, the drive that Windows 8 is installed on must also be encrypted by BitLocker.
- Any files saved to an encrypted drive will automatically be encrypted as well.
- Files remain encrypted only while they are stored on the encrypted drive. Files will be decrypted if they are copied on another drive, partition, or PC.
- Users who use BitLocker to protect the content of their personal files can also use File History as it seamlessly supports BitLocker on both source and destination drives.
- If you create a system image or backup of an unlocked encrypted drive, the files in the saved image or backup will be decrypted.
- If you share files with other people, such as through a network, the files are encrypted as long as they're stored on the same encrypted drive, and they can be accessed by authorized people or people you've given permission to.
- You will be able to unlock the encrypted Windows 8 OS drive at boot using either a password or a connected USB flash drive containing the startup key.
- If you select to use a USB flash drive to unlock the Windows 8 OS drive with at boot, then you will need to make sure that you have your BIOS or UEFI set to allow reading from a USB drives at boot. Most are by default.
- When using BitLocker with a TPM, it is recommended that BitLocker be turned on immediately after the computer has been restarted. If the computer has resumed from sleep prior to turning on BitLocker, the TPM may incorrectly measure the pre-boot components on the computer. In this situation, when the user subsequently attempts to unlock the computer, the TPM verification check will fail and the computer will enter BitLocker recovery mode and prompt the user to provide recovery information before unlocking the drive.
For more information, see: BitLocker Frequently Asked Questions (FAQ)
BitLocker Drive Encryption is only available in the Windows 8/8.1 Pro and Windows 8/8.1 Enterprise editions.
OPTION ONE
To Turn On BitLocker for Windows 8 OS Drive with or without a TPM
1. If you have not already, you will first need to do step 2, 3, 4, or 5 below for what you want to do.
2. Use REG File to Allow BitLocker to Encrypt OS Drive without a TPM
NOTE: This does the same thing as step 4 below, but automatically with a .reg file.
A) Click/tap on the Download button below to download the file below.
Enable_BitLocker_OS_Drive_No_TPM.reg

B) Save the .reg file to your desktop.
C) Double click/tap on the .reg file to merge it.
D) If prompted, click/tap on Run, Yes (UAC), Yes, and OK to approve merging.
E) Restart the PC to apply, and go to step 6 below to continue.
3. Use REG File to Require Additional Authentication at Startup with a TPM
NOTE: This does the same thing as step 5 below, but automatically with a .reg file. For example, to require USB at startup.
A) Click/tap on the Download button below to download the file below.
Enable_Additional_Authentication_BitLocker_OS_Drive_with_TPM.reg

B) Save the .reg file to your desktop.
C) Double click/tap on the .reg file to merge it.
D) If prompted, click/tap on Run, Yes (UAC), Yes, and OK to approve merging.
E) Restart the PC to apply, and go to step 6 below to continue.
4. Use Group Policy to Allow BitLocker to Encrypt OS Drive without a TPM
NOTE: This does the same thing as step 2 above.
A) Press the :winkey: + R keys to open the Run dialog, type gpedit.msc, and press Enter.
B) If prompted by UAC, click/tap on Yes.
C) In the left pane of Group Policy, click/tap on to expand Computer Configuration, Administrative Templates, Windows Components, BitLocker Drive Encryption, and Operating System Drives. (see screenshot below)
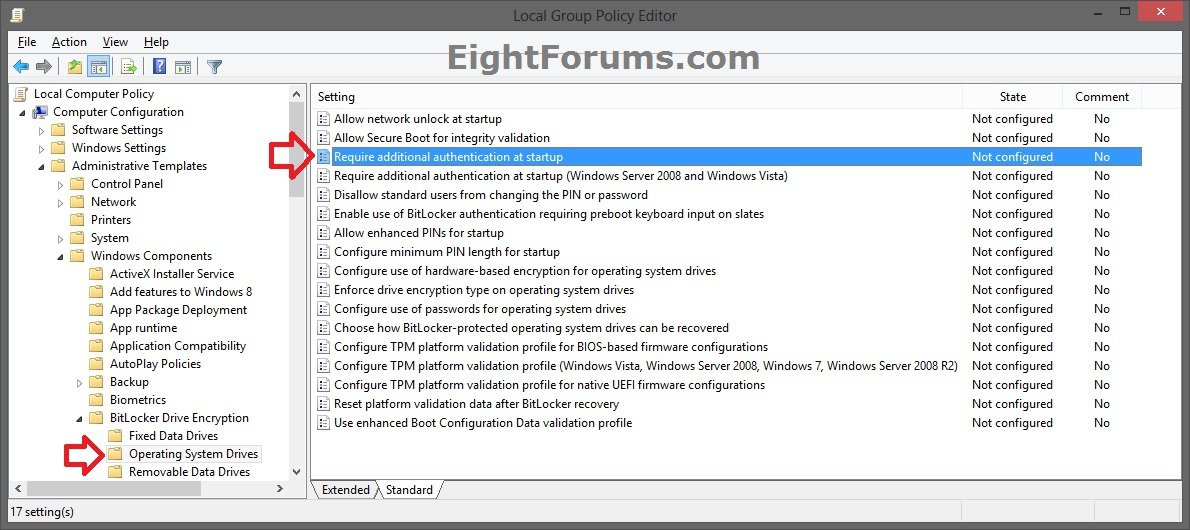
D) In the right pane of Operating System Drives, double click/tap on Require additional authentification at startup to edit it. (see screenshot above)
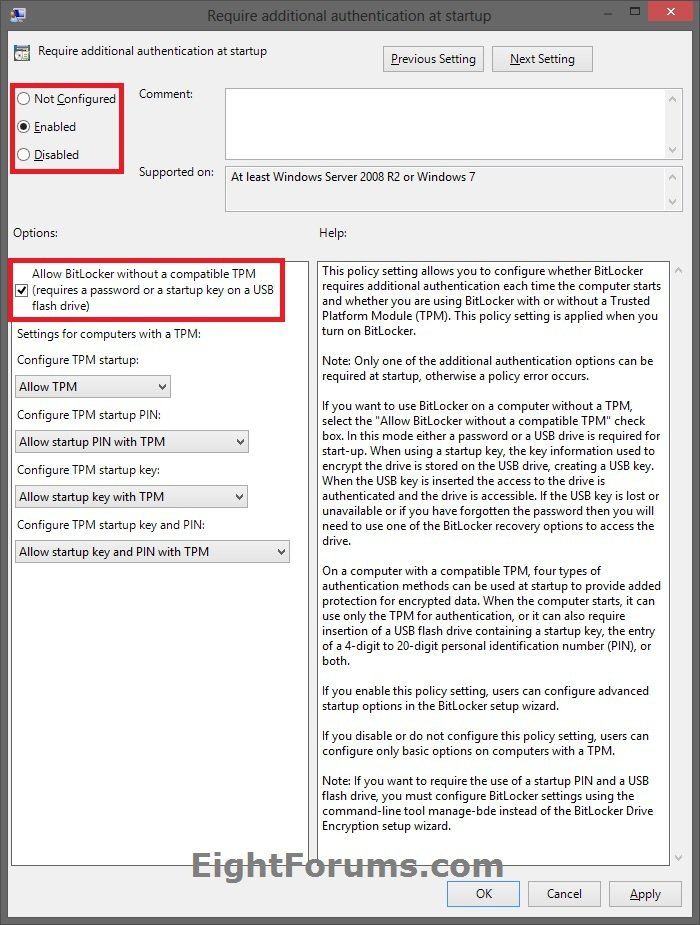
E) Select (dot) Enabled, check the Allow Bitlocker without a compatible TPM box, and click/tap on OK. (see screenshot below)
NOTE: Not Configured is the default setting.
F) Close Group Policy, and go to step 6 below to continue.
5. Use Group Policy to Require Additional Authentication at Startup with a TPM
NOTE: This does the same thing as step 3 above, but allows you to have more options.
A) Press the :winkey: + R keys to open the Run dialog, type gpedit.msc, and press Enter.
B) If prompted by UAC, click/tap on Yes.
C) In the left pane of Group Policy, click/tap on to expand Computer Configuration, Administrative Templates, Windows Components, BitLocker Drive Encryption, and Operating System Drives. (see screenshot below step 4C)
D) In the right pane of Operating System Drives, double click/tap on Require additional authentification at startup to edit it. (see screenshot above)
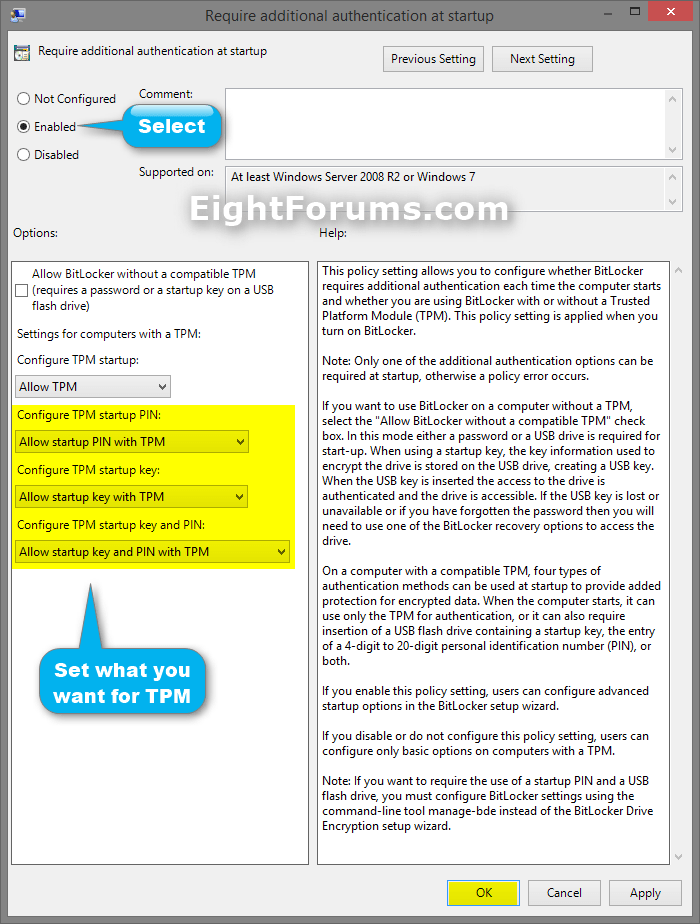
E) Select (dot) Enabled, uncheck the Allow Bitlocker without a compatible TPM box, and click/tap on OK. (see screenshot below)
NOTE: Not Configured is the default setting.
F) Close Group Policy, and go to step 6 below to continue.
6. If you have not already, choose to use either an AES 128-bit or 256-bit encryption method.
NOTE: Windows 8 uses AES 128-bit encryption by default.
7. Do step 8, 9, or 10 for how you would like to start to turn on BitLocker for the OS drive.
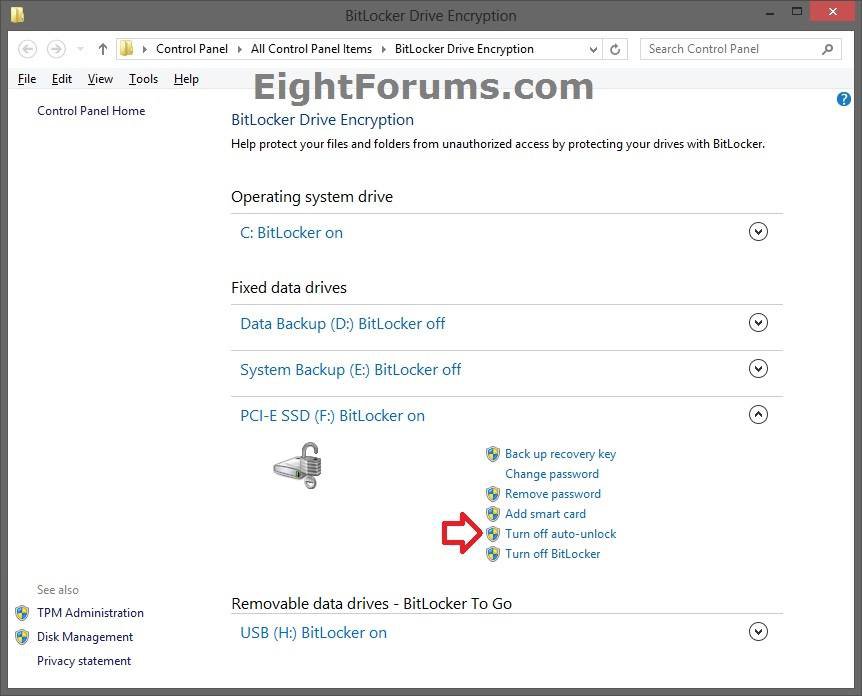
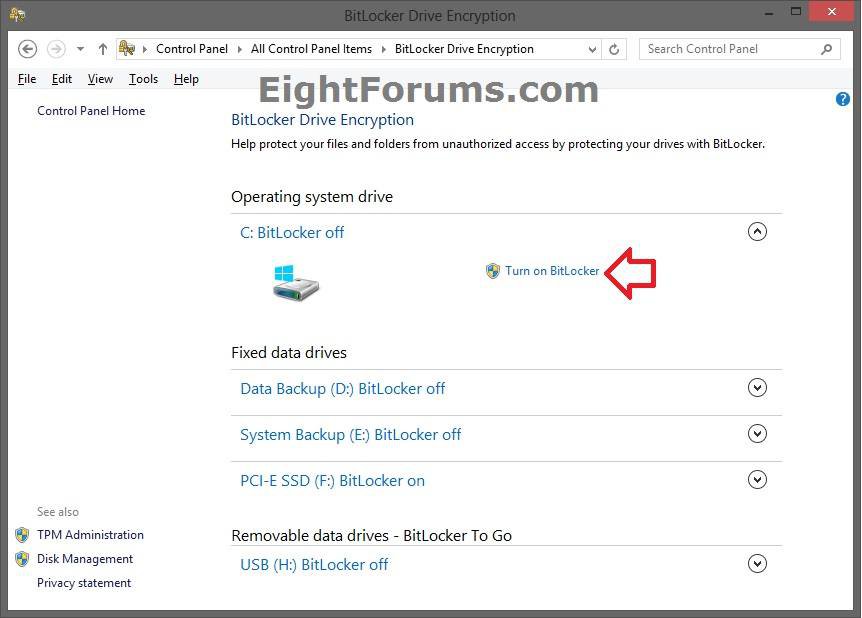
8. Open the Control Panel (icons view), click/tap on BitLocker Drive Encryption icon. Under Operating system drive, click/tap on an arrow to expand the Windows 8 drive you want to encrypt, click/tap on the Turn on BitLocker link, and go to step 11 below. (see screenshot below)
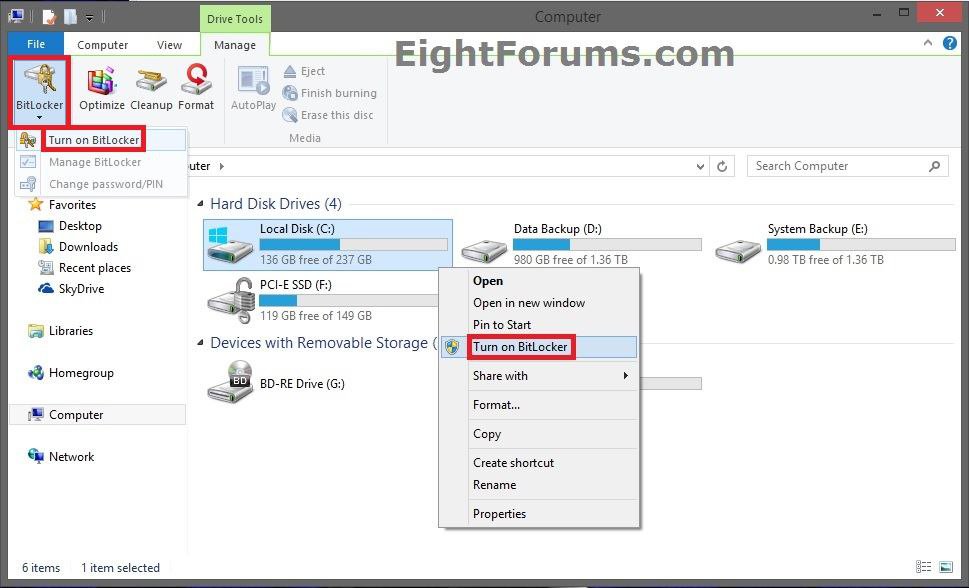
9. In File Explorer, open Computer/This PC, right click or press and hold on the encrypted Windows 8 drive you want to encrypt, click/tap on Turn on BitLocker, and go to step 11 below. (see screenshot below step 10)
10. In File Explorer, open Computer/This PC, select (highlight) the encrypted Windows 8 drive you want to encrypt, click/tap on Manage (Drive Tools) tab, click/tap on BitLocker icon in the ribbon, click/tap Turn on BitLocker, and go to step 11 below. (see screenshot below)
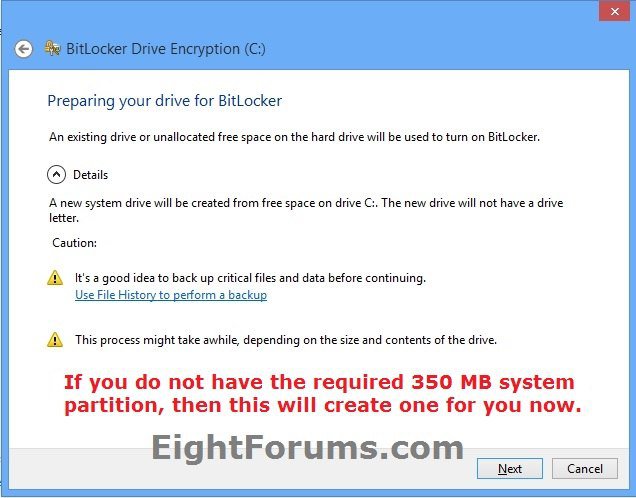
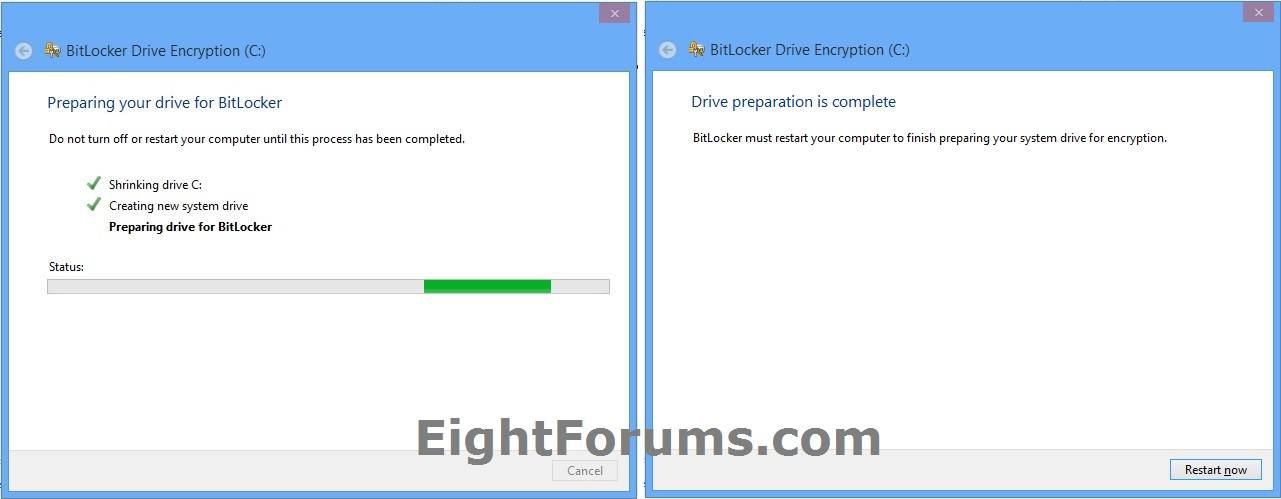
11. If you did not have the required 350 MB system drive partition, then BitLocker will now create one if able. Click/tap on Next, and Restart now when prompted. (see screenshots below)
NOTE: You will not get this step if you do already ave at least a 350 MB system drive partition.
12. Do step 13, 14, or 15 below for what you would like to use to unlock the Windows 8 drive with at startup. (see screenshots below)
NOTE: This will not be available with a TPM unless you did step 3 or 5 above.
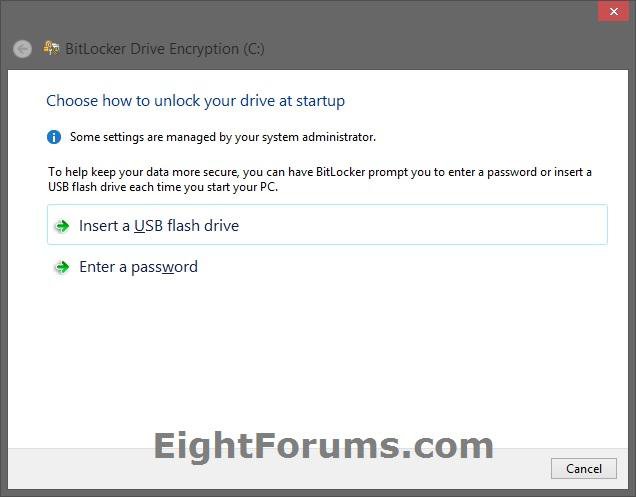
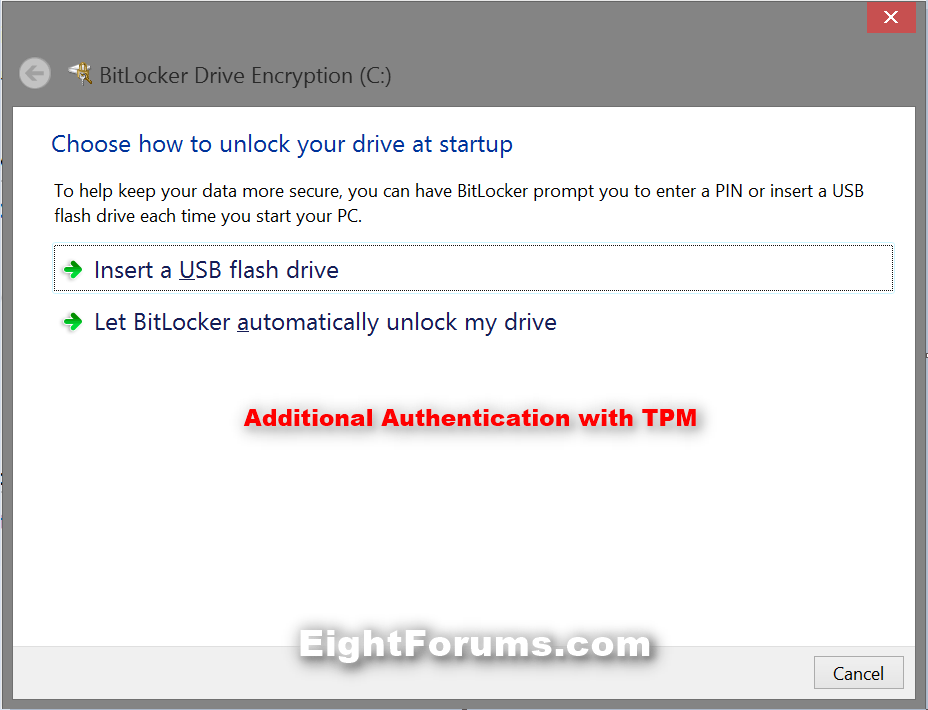
13. To "Insert a USB flash drive" at Boot to Unlock the OS Drive
NOTE: This will not be available with a TPM unless you did step 3 or 5 above.
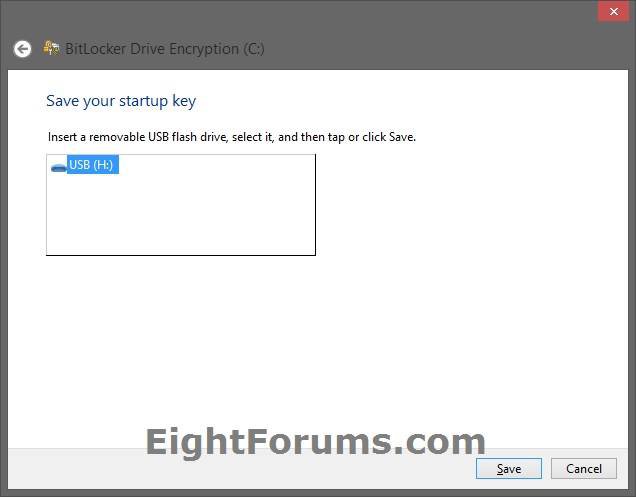
A) Connect a USB flash drive, and click/tap on the Insert a USB flash drive option. (see screenshot below step 12)
B) Select the USB flash drive you want to save the startup key on, click/tap on Save, and go to step 16 below. (see screenshot below)
14. To "Enter a password" at Boot to Unlock the OS Drive
NOTE: This will not be available with a TPM.
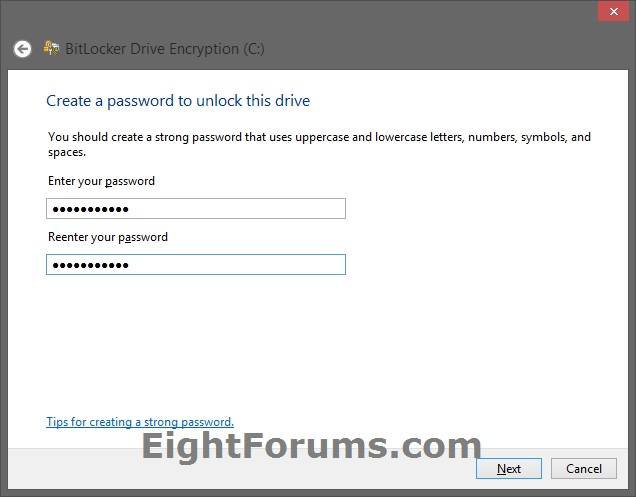
A) Click/tap on the Enter a password option. (see screenshot below step 12)
B) Enter and reenter a password at least 8 characters long, click/tap on Next, and go to step 16 below. (see screenshot below)
15. To Let BitLocker Automatically Unlock OS Drive
NOTE: This will only be available with a TPM.
A) Click/tap on the Let BitLocker automaticalyl unlock my drive option, and go to step 16 below. (see screenshot below step 12)
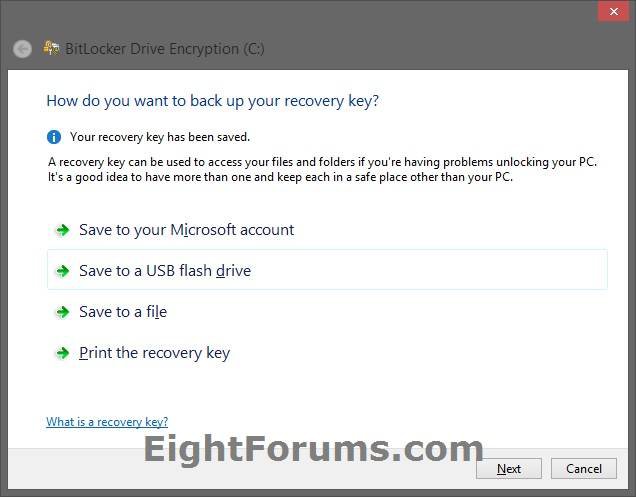
16. Select how you want to back up your BitLocker recovery key, and click/tap on Next when finished. (see screenshot below)
The Save to USB flash drive option will not be available if you are encrypting with a TPM. If you like, you could use the Save to a file option, and select a USB flash drive to save the file to though.
If you forget the password (step 14) or lost the USB flash drive (step 13), then you can still use this recovery key (a string of 48 random numbers) to get back into the OS drive at boot.
It's essential that you store a copy of your recovery in a safe place. If you lose it, you might permanently lose access to your files on the encrypted OS drive.
If you forget the password (step 14) or lost the USB flash drive (step 13), then you can still use this recovery key (a string of 48 random numbers) to get back into the OS drive at boot.
It's essential that you store a copy of your recovery in a safe place. If you lose it, you might permanently lose access to your files on the encrypted OS drive.
The Save to your Microsoft account option is only available on non-domain-joined PCs.
If you saved the BitLocker recovery key to your Microsoft account, you will be able to log in to your Microsoft account online at the Microsoft's site below from any PC to view all of your saved recovery keys at anytime.
http://windows.microsoft.com/recoverykey
If you saved the BitLocker recovery key to your Microsoft account, you will be able to log in to your Microsoft account online at the Microsoft's site below from any PC to view all of your saved recovery keys at anytime.
http://windows.microsoft.com/recoverykey
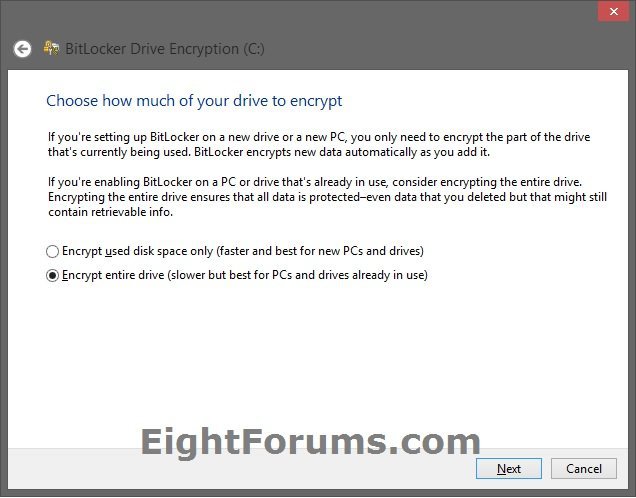
17. Select (dot) to encrypt entire drive, and click/tap on Next. (see screenshot below)
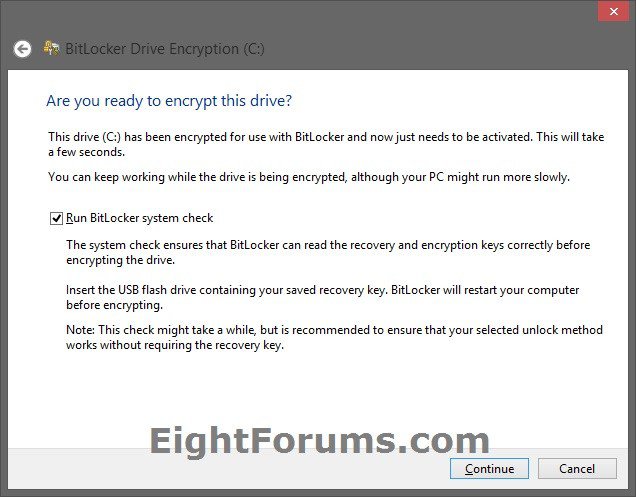
18. Check the Run BitLocker system check box, and click/tap on Continue. (see screenshot below)
NOTE: Running the system check is one more recommended way to make sure that BitLocker works smoothly for you, but it can take longer, and it requires your PC to restart. If you decide to run the system check, make sure you've saved your work before restarting. When your PC restarts, it will prompt you to unlock your operating system drive with the method you just chose in step 12 above.
19. You will now notice the BitLocker icon in the taskbar notification area. Click/tap on it, and on Restart now. (see screenshots below)
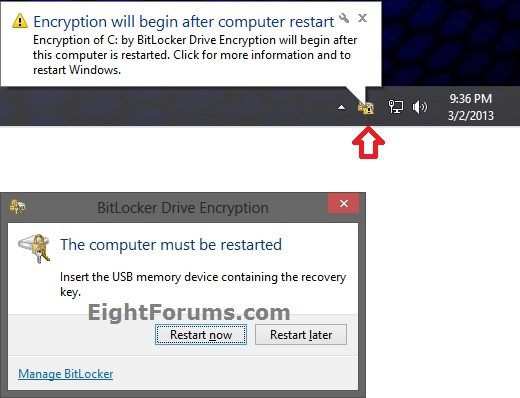
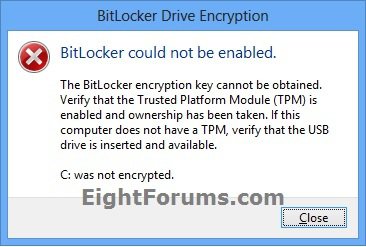
20. If the BitLocker system check failed from step 10 above, then you will see this below. Click/tap on Close. You are now finished since BitLocker was unable to encrypt the Windows 8 OS drive.
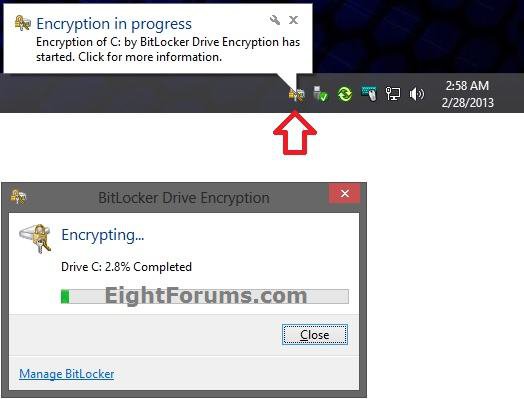
21. If the BitLocker system check was successful from step 18 above, then after a short moment you will notice the BitLocker icon in the taskbar notification area. You can click/tap on it to see the encryption progress. (see screenshot below)
NOTE: This may take a long time to finish, but you will still be able to use your PC during the encryption process. Just do not turn off the PC until it has finished encrypting.
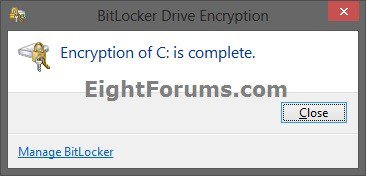
22. When encryption of the Windows 8 OS drive has finally finished, click/tap on Close. (see screenshot below)
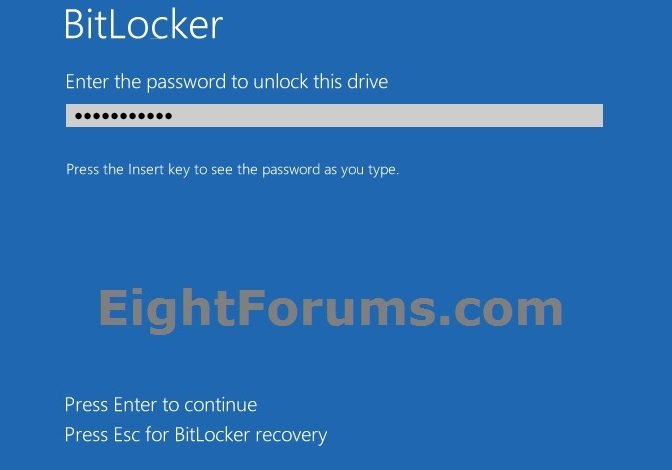
23. Whenever you start the Windows 8 PC, you may be required to either enter a password or connect the USB flash drive depending on what you selected in step 12 above.

OPTION TWO
To Turn Off BitLocker for Windows 8 OS Drive
1. If you have not already, you will first need to turn off auto-unlock for any encrypted fixed data drives. If you do not, then all fixed data drives that have auto-unlock turned on will also be decrypted at step 8 below.
NOTE: This does not apply to removable data drives.
2. Do step 3, 4, or 5 for how you would like to start.
3. Open the Control Panel (icons view), click/tap on BitLocker Drive Encryption icon, and go to step 6 below.
4. In File Explorer, open Computer/This PC, right click or press and hold on the encrypted Windows 8 drive you want to decrypt, click/tap on Manage BitLocker, and go to step 6 below. (see screenshot below step 5)
5. In File Explorer, open Computer/This PC, select (highlight) the encrypted Windows 8 drive you want to decrypt, click/tap on Manage (Drive Tools) tab, click/tap on BitLocker icon in the ribbon, click/tap Manage BitLocker, and go to step 6 below. (see screenshot below)
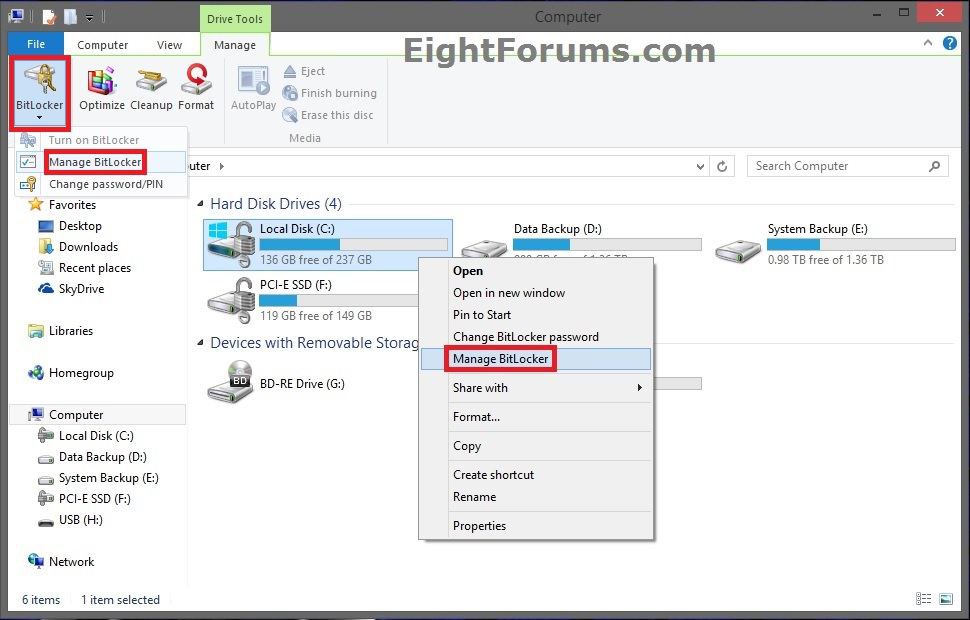
6. Under Operating system drive, click/tap on the arrow to expand the Windows 8 OS drive you want to decrypt, and click/tap on the Turn off BitLocker link. (see screenshot below)
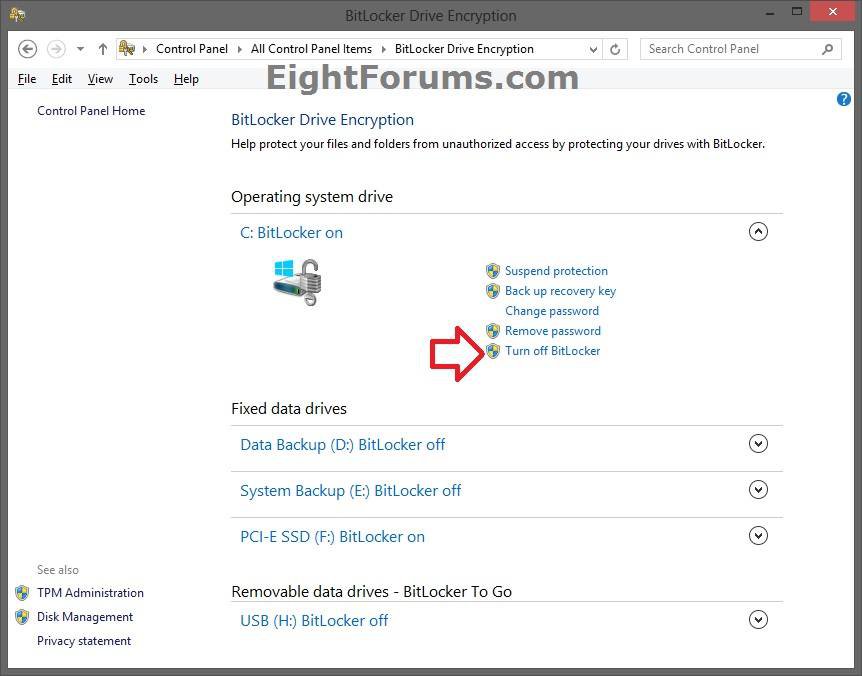
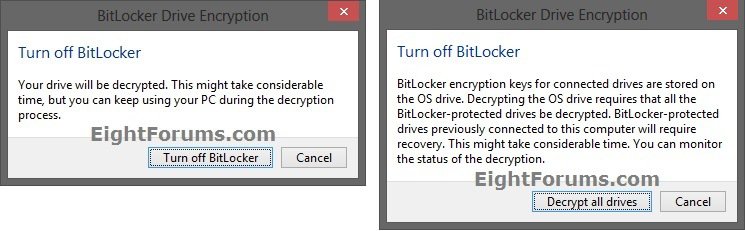
7. If prompted by UAC, click/tap on Yes.
8. Click/tap on Turn off BitLocker or Decrypt all drives depending in if you turned off auto-unlock for all fixed data drives in step 1 above. (see screenshots below)
NOTE: This may take a long time to finish, but you will still be able to use your PC during the decryption process. Just do not turn off the PC until it has finished decrypting.
9. You will now notice the BitLocker icon in the taskbar notification area. You can click/tap on it to see the decryption progress. (see screenshot below)
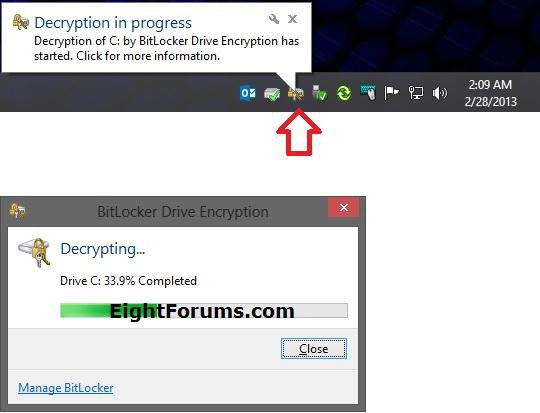
10. When decryption of the drive has finally finished, click/tap on Close. (see screenshot below)
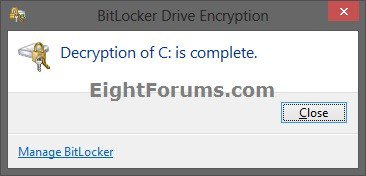
11. If you like, you could also do step 12 or 13 below to set the default setting to require BitLocker to only encrypt an OS drive with a TPM (step 2 and 4 in OPTION ONE) and not require additional authentification for a TPM (step 3 and 5 in OPTION ONE) if you like.
12. To Use a Reg File to Undo Step 2, 3, 4, or 5 in OPTION ONE
A) Click/tap on the Download button below to download the file below.
Disable_BitLocker_OS_Drive_No_TPM.reg

B) Save the .reg file to your desktop.
C) Double click/tap on the .reg file to merge it.
D) If prompted, click/tap on Run, Yes (UAC), Yes, and OK to approve merging.
E) Restart the PC to apply.
13. Use Group Policy to Undo Step 2, 3, 4, or 5 in OPTION ONE
A) Press the :winkey: + R keys to open the Run dialog, type gpedit.msc, and press Enter.
B) If prompted by UAC, click/tap on Yes.
C) In the left pane of Group Policy, click/tap on to expand Computer Configuration, Administrative Templates, Windows Components, BitLocker Drive Encryption, and Operating System Drives. (see screenshot below step 4C in Option One)
D) In the right pane of Operating System Drives, double click/tap on Require additional authentification at startup to edit it. (see screenshot below step 4C in Option One)
E) Select (dot) Not Configured, and click/tap on OK. (see screenshot below step 4E in Option One)
NOTE: This is the default setting.
F) Close Group Policy.
That's it,
Shawn
Related Tutorials
- How to Copy the BitLocker Startup Key for the OS Drive in Windows 8
- How to Turn On or Off BitLocker for Fixed Data Drives in Windows 8
- How to Turn On or Off BitLocker To Go for Removable Data Drives in Windows 8
- How to Suspend or Resume BitLocker Protection of a Drive in Windows 8
- How to Choose BitLocker Drive Encryption Method and Cipher Strength in Windows 8
- How to Turn On or Off Auto-unlock of BitLocker Encrypted Data Drives in Windows 8
- How to Back Up the BitLocker Recovery Key of a Drive in Windows 8
- How to Unlock a Drive using BitLocker Recovery in Windows 8
- How to Use BitLocker Repair Tool to Recover a Drive in Windows 7 and Windows 8
- How to Change or Reset the BitLocker Password of a Drive in Windows 8
- How to Allow or Prevent Standard Users from Changing BitLocker Password or Pin in Windows 8
- How to Check BitLocker Status of Drive in Windows 7 and Windows 8
Attachments
Last edited by a moderator: