I have a admin account and a normal user account say XXX.
I have a drive (say Z), to which I want to restrict access to the user XXX. The user should be able to read the documents and view the videos in the drive. However, he should not be able to delete/modify the files in the drive or write new files to the drive.
I have gone through: Permissions - Allow or Deny Access to Users and Groups in Windows 8. I'm not comfortable with command prompts or registry keys, so I tried option three (Change Access Permissions in Advanced Security Properties).
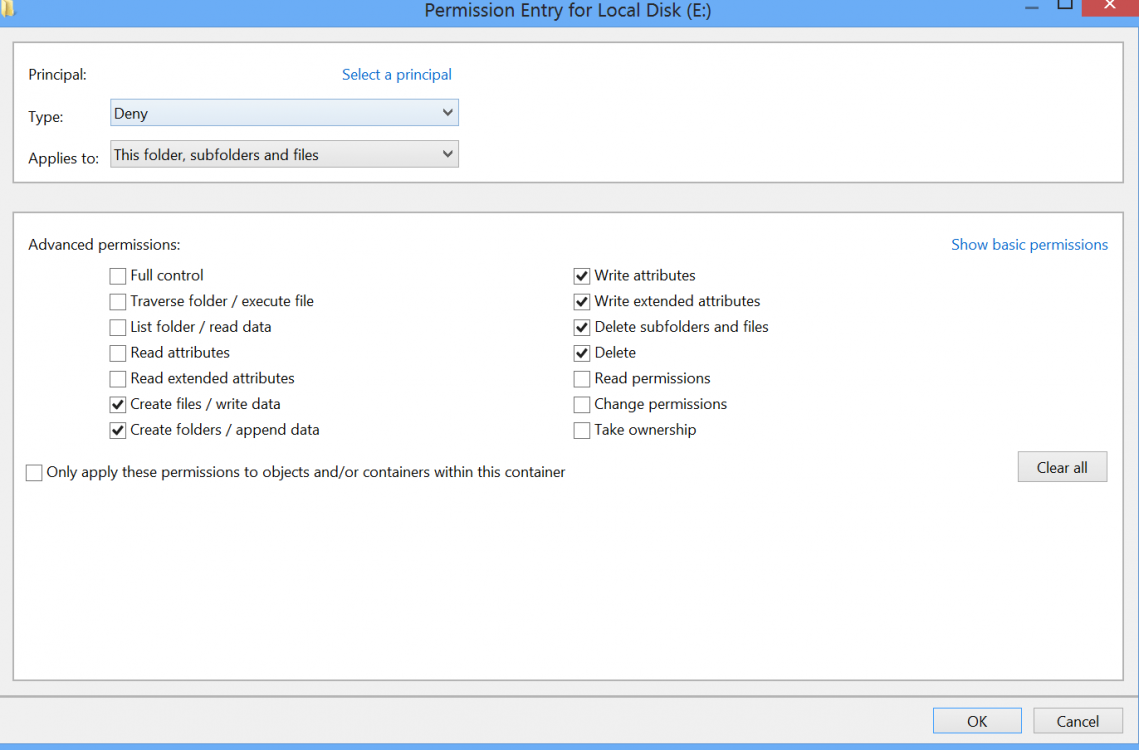
By default, the user had permission for "Read, Read & execute, List folder contents" only. However, even with these I found that the user could delete and modify the files/folders in drive Z. So, I denied the following: "Create file/folders, write attributes/extended attributes, delete subfolders/files". This seems to serve my purpose.
Now I wish to know two things:
1) Am I doing the right thing or messing up something?
2) There was a radio button "Only apply these permissions to objects and/or containers within this container". This I had left unchecked. Should I check this? The window (see attachment) clearly states that these permissions apply to "this folder, subfolder and files". Is this just a redundant option?
Thanks!
I have a drive (say Z), to which I want to restrict access to the user XXX. The user should be able to read the documents and view the videos in the drive. However, he should not be able to delete/modify the files in the drive or write new files to the drive.
I have gone through: Permissions - Allow or Deny Access to Users and Groups in Windows 8. I'm not comfortable with command prompts or registry keys, so I tried option three (Change Access Permissions in Advanced Security Properties).
By default, the user had permission for "Read, Read & execute, List folder contents" only. However, even with these I found that the user could delete and modify the files/folders in drive Z. So, I denied the following: "Create file/folders, write attributes/extended attributes, delete subfolders/files". This seems to serve my purpose.
Now I wish to know two things:
1) Am I doing the right thing or messing up something?
2) There was a radio button "Only apply these permissions to objects and/or containers within this container". This I had left unchecked. Should I check this? The window (see attachment) clearly states that these permissions apply to "this folder, subfolder and files". Is this just a redundant option?
Thanks!
Attachments
My Computer
System One
-
- OS
- Win 8