You are correct that one would need an AV and other security measures to protect against malware, but...
AV will stop known malware, but pretty much useless against unknown ones and as such, the AV definition update is critical for the detection. It is also important to keep the system/applications security patches up to date, don't logon with the admin account, and use additional security protection such as MS EMET, Winpatrol, etc., to keep the malware off of a system.
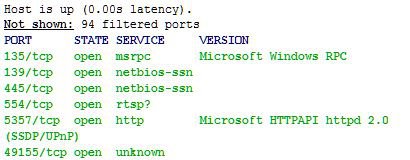
Shields Up only sees ports that allow inbound connection from any IP address when it scans for open ports, or services, and it cannot scan for "uninvited vulnerabilities".
This is due to how these uninvited programs work. Once the malware establishes itself on a system, it contacts the command and control center, or CCC, for instruction on a periodic basis. The connection initiated by the host can be on any ports, that does not really matter. What matters is that the destination of this connection is defined within the malware code. It's pretty much a point-to-point connection that does not show up in the port scan, even in nMap, as an open port.
In theory, my Windows 8.1 could have malware running it; the nMap scan posted earlier cannot determine the existence of the malware and there's no easy way to see, if the system is infected with just a port scan. One would need to analyze running processes, established outbound network connections, and capture the network traffic on a switch/router to reasonably determine the existence of malware. That is especially true with the "industrialized/modern" malware that is hard to detect.
PS: Thanks for "thumbs-up"!