Hi Folks,
I'm browsing through my windows firewall settings and I'd like to disable everything that's not required for proper operation.
It is my opinion that the more stuff that is disabled in my computer system, the more secure it is.. Anyone have a different opinion?
I already went through Services.msc and disabled stupid things like telephony and remote desktop connection and things that I'll never use.
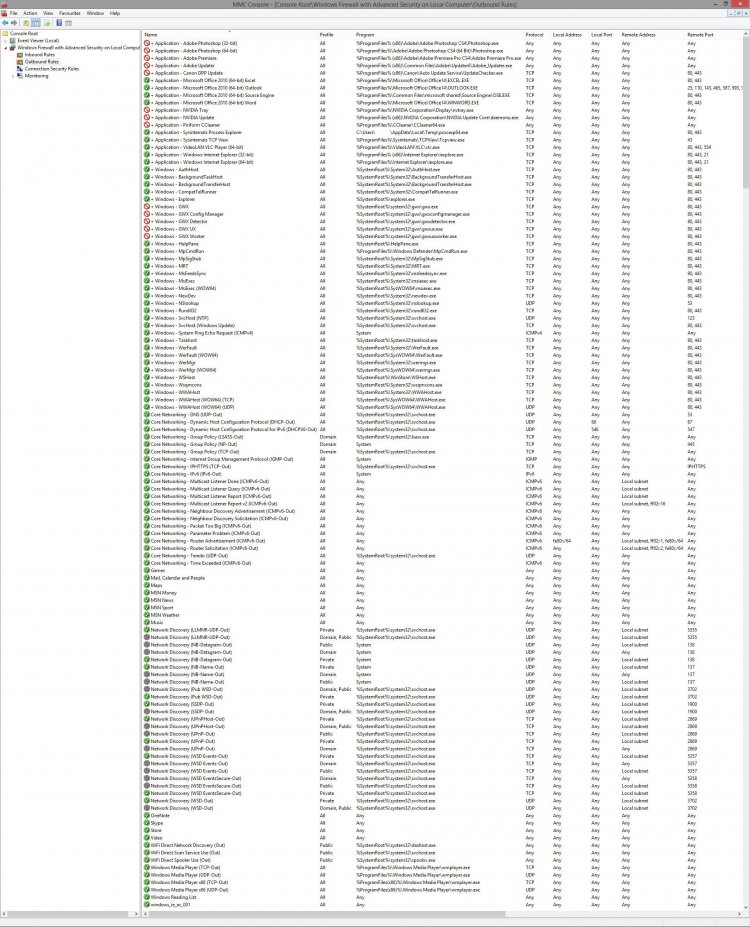
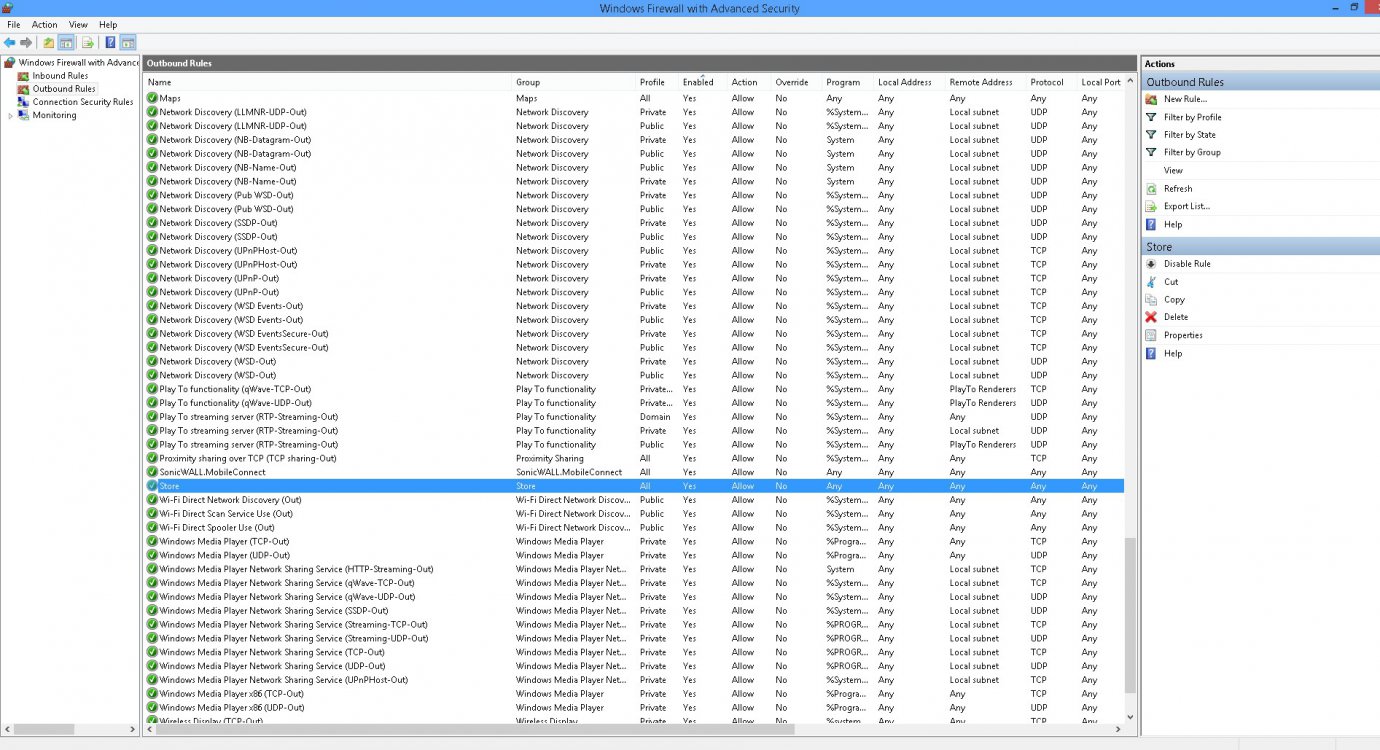
Inside the Windows Firewall advanced settings, can I disable all the windows media player sharing service stuff? I use windows media player to play music and movies but I certainly don't do any sharing with it.
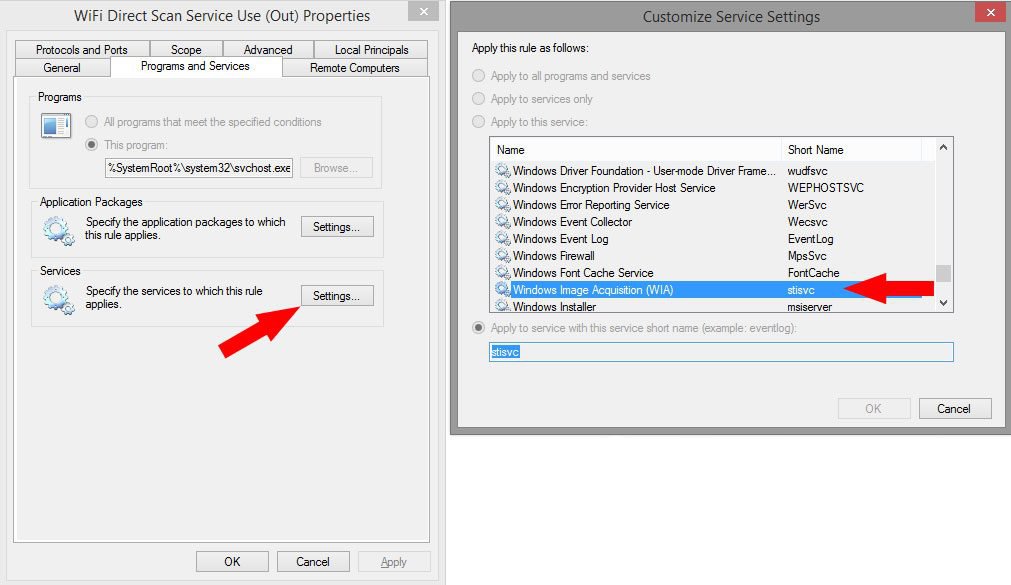
What about wifi direct scan and wifi driect network discovery... My desktop pc is hardwired (cat5).. I don't need any of that stuff right?
Sonic Wall mobile content??? Huh?
What about Play To Streaming Server ??
More to follow!T
thanks
I'm browsing through my windows firewall settings and I'd like to disable everything that's not required for proper operation.
It is my opinion that the more stuff that is disabled in my computer system, the more secure it is.. Anyone have a different opinion?
I already went through Services.msc and disabled stupid things like telephony and remote desktop connection and things that I'll never use.
Inside the Windows Firewall advanced settings, can I disable all the windows media player sharing service stuff? I use windows media player to play music and movies but I certainly don't do any sharing with it.
What about wifi direct scan and wifi driect network discovery... My desktop pc is hardwired (cat5).. I don't need any of that stuff right?
Sonic Wall mobile content??? Huh?
What about Play To Streaming Server ??
More to follow!T
thanks
My Computer
System One
-
- OS
- Windows 8.1 Pro
- Computer type
- PC/Desktop
- CPU
- PentiumD
- Motherboard
- Intel
- Memory
- 4 Gigs